Self-Sovereign Identity, and Why Every Malaysian Needs One
*Disclaimer: The content is written solely from my own thoughts & imagination of how it can potentially work, and may not be the actual representation of the implementation.
This, is a Malaysian’s identity card.
Your identity card is a very powerful possession. It grants you the ability to create bank accounts, apply for investment & financial services, enroll into education courses, job application, driving license, fly domestically, visit a doctor in a hospital and many more. On a side note, it also has a Touch n Go feature that allows the card to be use to pay for tolls & public transportation around Malaysia.
It is also the most important card that you cannot live without because this card defines your birthright of your country & proof of your true identity to others. It contains many different essential information such as a 12-digit numbers that determine your birth date, place of birth & gender, with addition of a photo to identify what you look like & biometrics that links to your fingerprint identity. Whether if you want to apply for loans, job applications, education, bank accounts or any other form of application, an identity card is always required as a prerequisite for these applications. You can find out more interesting information about your identity card in Wikipedia.
However, with every benefit you yield with your IC card comes unforeseen cracks underneath that your true identity is actually at risk.
Problems with Current Identification Systems & Its Effects
Let’s start with the current method of obtaining personal information for any type of essential applications. Whenever you sign up for something important that requires your identification, your personal data such as your name, home address, phone number, email address & other sensitive data will be kept with third-party organizations, such as government bodies, financial companies, the companies that employed you and the businesses you dealt with. This is because they need proof that the person of interest is who he or she claims to be.
According to Malaysia’s Official Portal of Department of Personal Data Protection, you, as a user or consumer, have the right to:
Access personal data whenever necessary.
Make corrections on your personal data that have been processed.
Withdraw consent to process personal data if it’s not in used.
Audit if your personal data is processed improperly for direct marketing purposes.
Prevent your data being processed for other purposes than the intended.
However, every time we apply for something, third-party organizations such as companies will always ask you to sign a long-ass data privacy terms & conditions, telling you how they would and would not use your data. Normally, you wouldn’t even bother reading it because either it’s too wordy and you don’t have the time, or you may be illiterate. As a result, when you signed the document, third party organizations may use for other means such as sharing your personal information to other companies for provide better customer experiences and marketing purposes. Even if they tell you they won’t, how do you even know? Do you trust them with a piece of paper that you signed? How do you verify that they did not share your personal information? The answer is that you won’t know, and most of you will not be bothered as long as it doesn’t affect your life.
Second, identity card is a form of physical identification that can be easily lost or stolen if you did not safeguard it properly. Most of us keep our identity cards in our wallets and take it wherever we go. For guys, if your pants don’t have deep pockets, you’ll have the tendency to drop your wallet somewhere, especially when you’re sitting in a crowded restaurant. For ladies that do not have much accessibility to pockets, you will bring your handbags or carry your wallets around by hand, which makes you the perfect prey for snatchers to steal your wallet or handbag, alongside your most important card in the world with it.
Furthermore, have you experienced replacing your identity card after losing it? It can be a hassle if you need to walk-in to any government office especially during peak hours when it’s very crowded, thus depending on how swift & efficient is the customer service at different branches, you may have to wait for hours to apply for replacement.
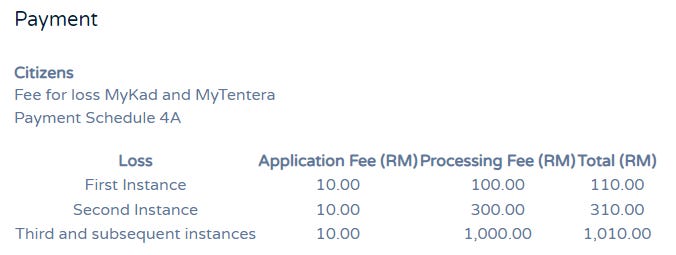
Not to mention you’ll have to pay a hefty fee in between RM 110 up to RM 1,010 for the replacement fee. For someone earning a minimum monthly wage of RM1,500, that’s already 7% of your wage. Imagine if you got your identity card stolen two more times even though you are already very careful with how you keep your identity card, replace one at least for the 3rd time will cost you a whopping 67% of your minimum monthly wage!
Other than your physical identity, let’s also talk about your login credentials. Every time you visit a website to access a service, purchase something online or read your email, you’ll need to create a login ID & password. You may think the login ID you create is yours but technically the ID is owned by the third-party that stores your ID & credentials in their database. Using a login ID poses two risks:
Centralization risk that the third-party may terminate your services at any time if you breach any of their terms & conditions.
Data breaches to which the hacker stole users’ personal data to perform malicious act.
In the world of social media, the moment you are posting your dog pictures or meal of the day is another piece of information collected by the likes of Facebook, Instagram & Google to understand you better than maybe your husband/wife can. Huge companies such as these are earning billions in revenue using our personal information as a marketing tool to target you advertisements, while also left you exposed to hackers & earned you zero for using your data.
Likewise in a real-life situation, stateless people is also a huge issue in Malaysia. Foreigners who are women and married to Malaysian men can’t be registered as Malaysian citizens, which also mean they do not have an identity card as proof of their citizenship. Worse of all, if these women are unable to provide marriage certificates proving that they married to Malaysian men, their children will also be stateless and without a proper identification. The catastrophic consequences are that they are unable to provide sufficient documents for employment thus have to work in a gig economy.
It’s clear to see we need a better solution to own our identity & protect our personal data from these external risks. Let’s take a detailed look at the potential solution that may change how we truly own our personal data & protect it.
Solution: Blockchain-Based Decentralized Identifier (DID) & Verifiable Credentials
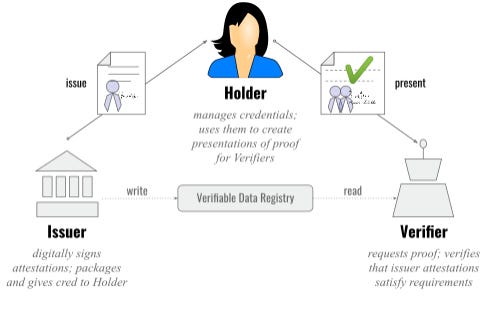
Decentralized Identifier (DID) is a cryptographically verifiable identifier that is created and owned by the user, without control from centralized entity & does not contain personally identifiable information without disclosure. Verifiable credentials are tamper-proof credentials that are to be presented for verification (such as licenses or passports). DID & verifiable credentials work on a trust model between 3 parties: issuer, holder & verifier.
The issuer is the entity that issues a unique ID to you, the holder. Normally, the issuer can be a government issuing a citizen ID, your university issuing your student ID, or your employer issuing your employee ID. In a blockchain setting, you have to remember that your wallet has two types of keys: a public key & a private key. Your public key is like a gateway to authenticate your identity, then you’ll need to use your private key to sign & approve the identity transaction. Every issuer, holder & verifier will have its own public & private keys. (*Note: Always remember to keep your private key safely and do not reveal it to anyone else). The key point is that your sensitive personal data are always encrypted and will never be exposed unless someone gets hold of your private key or seed phrases.
As a holder, you can store all of your important personal data & credentials, such as your passport, academic certificates, job certificates, health records, driving license and many more. Whether you want to apply for a bank account, travel around the world or register anything, your newly created DID will be the focal point for identity verification, and your personal data will always be held in your wallet and will never be stored by any third-party organizations.
Let’s make an example of how to apply for an IC using the DID method. Let’s say you reached the age of 12 and you want to create an IC to validate you as a citizen of Malaysia. When you want the government to issue an IC using the blockchain, you’ll have to submit the necessary information like your name, birth date, birth place, the name of your parents, etc. In return, the government will generate a fixed string of alphabets & numbers called a hash as an output. A hash is basically encrypted & irreversible, meaning whatever input data that you use to generate the hash, you can’t reverse engineer back to the input data which makes it resilient against hackers trying to access your data. For the issuer, all your necessary information will be converted into a hash, then the hash will be signed by the government & sent to your wallet, while keeping a copy of the hash themselves. The hash will work more or less similar to your IC number, and it will be made public in the blockchain especially for companies or businesses that requires verification.
Now let’s say you want to apply for a bank loan in Maybank. Maybank wants to verify that you’re a legal citizen of Malaysia, which makes them the verifier. Each time when Maybank wants to perform a verification, instead of Maybank asking you to fill up forms, Maybank shares you a QR code that contains their own hash with the necessary information they need to verify you. Using your wallet’s QR code which has your hash in it, a comparison will be made between your hash & Maybank’s to see if they are identical. Then they’ll also reference your hash to the duplicated hash held by the government to verify the hashes are a match. Finally, your identity is verified without the need for you to fill up your personal details & submit to Maybank for safekeeping. Do take note that your personal details are not reviewed to the third-party organization.
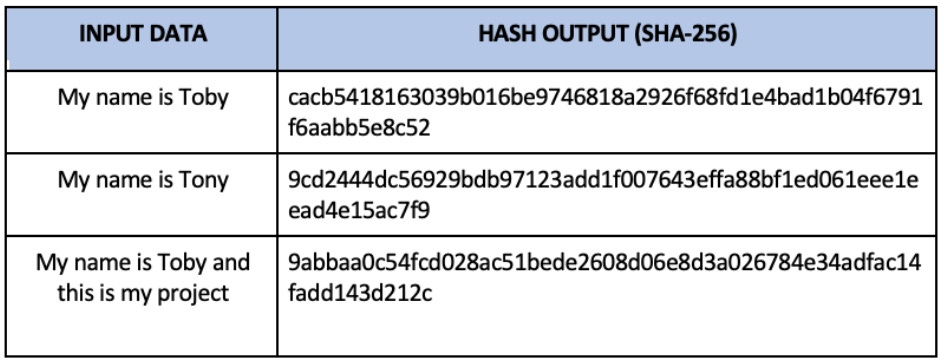
To give an example in layman terms, your bank detects a hash of “a89jndf09784….” that represents your birth date; or “9sahj34553jkhnm1560…..” that represents your driving license. This enhances security in a way that Maybank does not store all customer’s information in a database, thus giving the responsibility of protecting your data back to the holder, in addition to removing cost of database storage & maintenance. Whenever Maybank wants to re-authenticate you again, they can always look up to your hash that is publicly available in the blockchain.
In summary, this system benefits all 3 parties in that:
(a) The issuer is able to effectively save a lot of time to process an application & verification for a unique DID.
(b) The holder gets to own their personal data & credentials without third-party control, which reduces third-party risks of data breach & identity theft.
(c) The verifier is also able to effectively save a lot of time to process an application & verification for any services you request.
Furthermore, decentralized identifiers have many other benefits such as:
Advantageous especially for stateless people. If a foreigner marries a Malaysian, stores a digital proof of a marriage certificate in a wallet in a form of a soulbound token (publicly verifiable, non-transferrable NFT), then the foreigner is able to prove his citizenship to employers or any other third party organizations effectively with his/her DID without delay.
You, as a holder, are able to self-manage and monetize your data to third-party companies if they plan to use your data to advertise suitable products & services to you.
It is very hard to duplicate a cryptographically proven identity, so no one can fake a signature to sign transactions as long as you keep your private key safe.
Conclusion
Decentralized identifiers are still a new technology yet to be explored & widely adopted. It takes time to develop the right systems to make the process of issuing decentralized identities a reality. Audits & more social experiments are needed to provide quality feedback to Malaysia governments & organizations to issue IDs securely, privately & efficiently. Imagine if everyone has a designated DID & private crypto wallets, everyone gets the right to own & protect their wealth & identity. To me, this combination alone can be the sole reason why I’m very bullish on on the future of blockchains & cryptocurrencies. With DIDs & private wallets, users can power decentralized economies where every single transaction is done peer to peer & also in a secure & transparent manner.
Bonus: Crypto Self Custodial Wallet = Decentralized Verifiable Credential?
As a matter of fact, the current crypto self-custodial wallets, such as Metamask, are actually already using a form of verifiable credential where Metamask is the issuer, you are the wallet holder and the DApps (decentralized applications) & DeFi (decentralized finance) are the verifiers. Each wallet has a public key & a private key, where the public key can be identified by anyone, but to be able to use a service, the verifier will need the holder’s permission & approval to access the user’s funds and perform an action. Users are able to connect to an app or service and disconnect whenever not in use, thus the app does not store your wallet information, while the holder is the custodian of his/her assets & keys. However, holders may still need to revoke token approvals/permissions to ensure the smart contract of a DApp does not take control of your assets after you have given permission to do so.